How To Install Cowpatty In Windows 7
Depending on the prerequisites of your course, you may want to cover these in more or less detail. Stakeholders: Players in the Systems Game A stakeholder is any person who has an interest in an existing or proposed information system. Types of Information Systems Transaction processing systems (TPS) Management information systems (MIS) Decision support systems (DSS) Expert systems (ES) Communications systems Collaboration systems Office automation systems Teaching Notes These definitions can be useful to help students understand what an information system is in all its varieties and flavors. Stakeholders can be technical or nontechnical workers. Business drivers that influence information systems development.
Cowpatty: disgusting name, serious network tool.Authored by Joshua Wright, Cowpatty provides hackers, attackers, and network administrators with a way to implement offline dictionary-based attacks against wireless system. 
Jacuzzi bath tub manuals. I would search your breaker panel for a circut breaker titled jacuzzi tub (or something to that effect), and if it is not listed I would get someone to monitor when the tub shuts off, while you flip each breaker off, one at a time so as to determine which breaker it is and then immediately title it. After access is gained, inspect the pumps receptacle and if it is not GFIC protected I would return to the breaker panel, it may have a GFIC breaker. If neither are the case, then have this issue repaired The button on your jacuzzi is air actuated with a flexible air line that connects to the actual switch, it may have broken or however became disconnected. Any questions, feel free. Next, an access panel to the tubs motor should be installed.
Ways To Install Windows 7
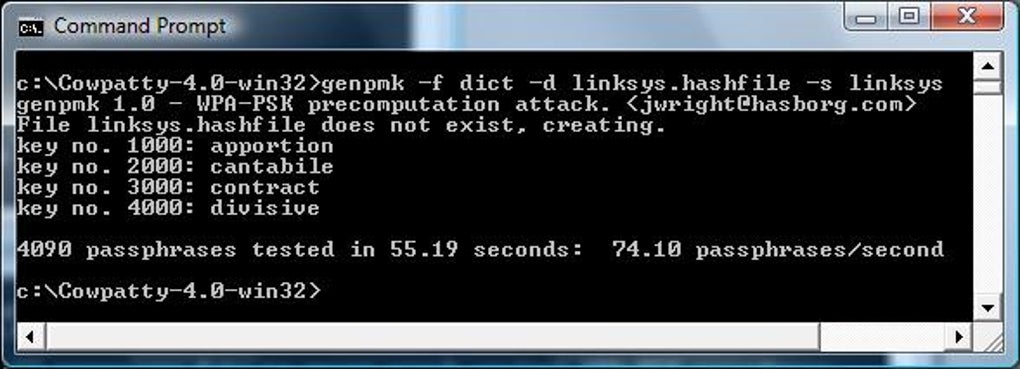
As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords, coWPAtty. In this tutorial, we’ll use the piece of software developed by wireless security researcher Joshua Wright (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords. It is easier than you think, so let’s get to it! Step 1: Find the Cowpatty Cowpatty is one of the hundreds of pieces of software that are included in the BackTrack [] and Kali [] OS’s.


If you are using a different Distro, you can download and install. For this demo, I will be using BackTrack. For some reason in BackTrack, it was not placed in the /pentest/wireless directory, but instead was left in the /usr/local/bin directory, so let’s navigate there.